Cyber Security of Complex Systems
Workshop of 60th IEEE Conference on Decision and Control
Enter Here
 |
Previous Workshop IFAC World Congress 2020 Slides Download Here
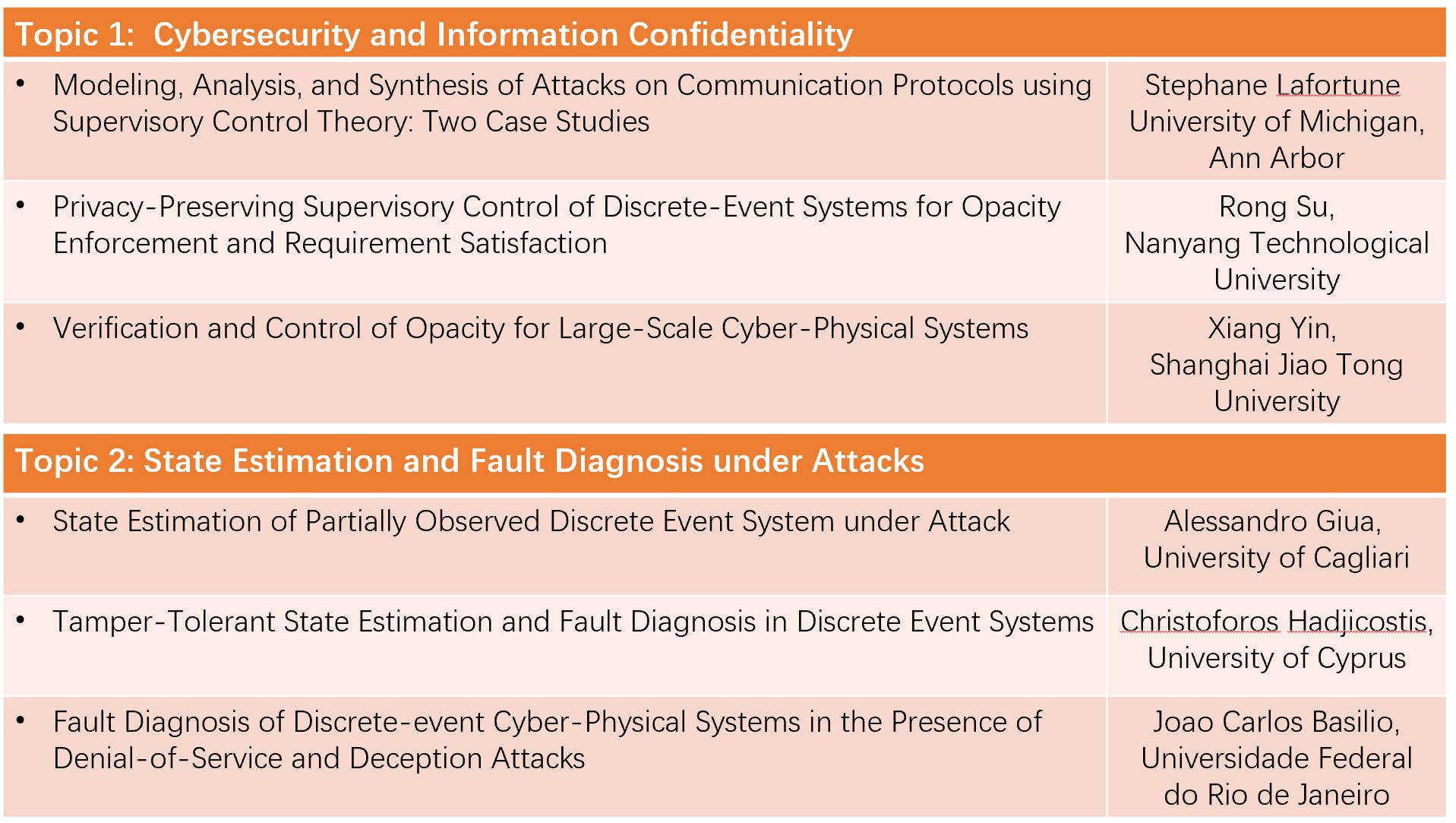
Cyber Attacks Based on DES
A detailed account of most recent research outcomes is provided on fault diagnosis, opacity analysis and enhancement, and cyber security analysis and enforcement, within suitable discrete event system modelling frameworks. In each case, we describe basic problem statements and key concepts, and then point out the key challenges in each research area. After that, we present a thorough review of state-of-the-art techniques, and discuss their advantages and disadvantages. Finally, key research directions for further exploration is highlighted.
 |
With the continuous advancement of information and communications technology (ICT), in particular, the recent 5G-based IoT technologies, we are enjoying unprecedented connectivity around the world, including the ability to remotely monitor and control various systems and processes. At the same time, the threat of cyber attacks that may potentially cause significant system damage and even cost human lives, is increasingly attracting attention from different research communities. Within the DES community, different attack models have been proposed and analysed, upon which relevant defense techniques have been developed.
Research Topic
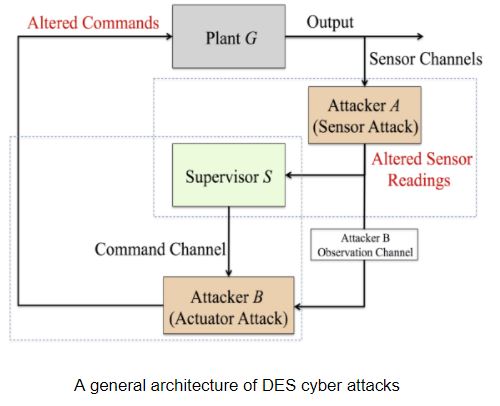
1.Attack of Observation Channels
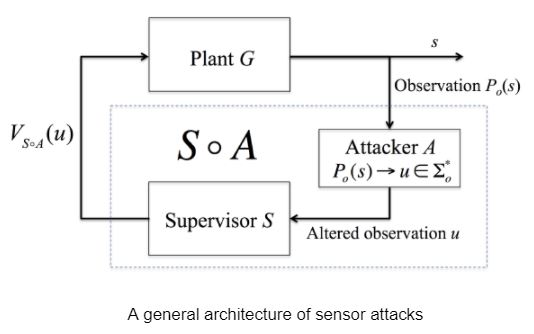 |
A given closed loop system 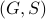 is attackable if there exists a non-empty attack model
is attackable if there exists a non-empty attack model 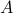 such that the following hold:
such that the following hold:
1. Covertness: Event insertions by 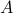 must be convert to
must be convert to 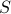 , i.e.,
, i.e.,
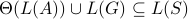 ,
namely the supervisor will not see any unexpected observable sequences from
,
namely the supervisor will not see any unexpected observable sequences from 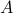 that are allowed by the plant
that are allowed by the plant 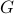 .
.
2. Strong attack: 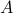 may always cause “damage” to
may always cause “damage” to 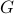 , i.e.,
, i.e.,
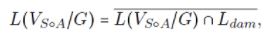 |
Weak attack: 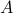 may possibly cause “damage” to
may possibly cause “damage” to 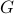 , i.e.,
, i.e.,
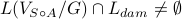 ,
namely some string in the closed-loop system
,
namely some string in the closed-loop system 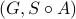 is a damaging string.
3. Control Feasibility: The closed-loop language is normal with respect to
is a damaging string.
3. Control Feasibility: The closed-loop language is normal with respect to 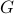 and
and 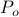 , i.e.,
, i.e.,
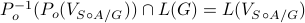 .
The attack model
.
The attack model 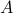 defined above is called an Attack with Bounded Sensor Reading Alterations(ABSRA) of
defined above is called an Attack with Bounded Sensor Reading Alterations(ABSRA) of 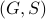 .
.
2.Attack of Command Channels
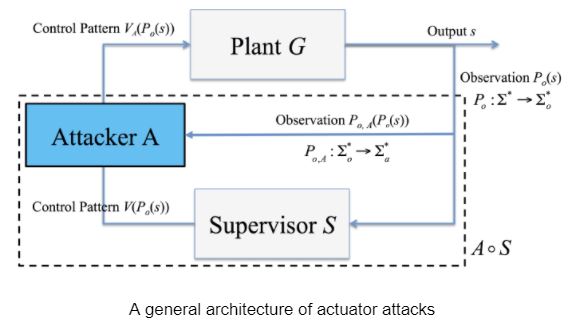 |
An actuator attack model is described as a map
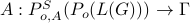 , which maps each attacker's observation $(P_{o,A}(P_o(s)), V(P_o(s)))in (Sigma_{o,A}cup
, which maps each attacker's observation $(P_{o,A}(P_o(s)), V(P_o(s)))in (Sigma_{o,A}cup
{epsilon})times Gamma$ to an altered control pattern.
(Attackability) Given a plant 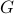 and a normal supervisor
and a normal supervisor 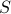 , whose supervisory control map is
, whose supervisory control map is 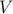 , the closed-loop
system
, the closed-loop
system 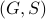 is attackable with respect to an attack model
is attackable with respect to an attack model 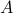 associated with
associated with 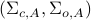 and a
damaging language
and a
damaging language 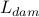 if
if
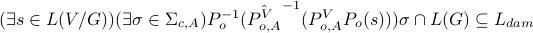 ,
where
,
where 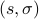 is called an attack pair under
is called an attack pair under 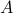 .
.
3.Attack of Observation Channels and Command Channels
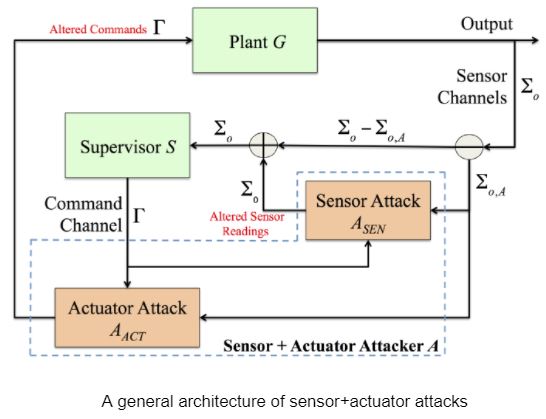 |
and an actuator attack 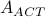 , where
, where
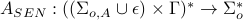 ,
and
,
and
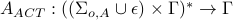 ,
where the attacker can apply observations of both intercepted events and control patterns to sensor and actuator attacks.
,
where the attacker can apply observations of both intercepted events and control patterns to sensor and actuator attacks.
Team members
Lin Liyong, Tai Ruochen, Zhu Yuting
Publications:
Tai, R., Lin, L., Zhu, Y. and Su, R., 2021. Privacy-Preserving Co-synthesis Against Sensor-Actuator Eavesdropping Intruder. arXiv preprint arXiv:2104.14919, Automatica, under review, 2021.
Tai, R., Lin, L., Zhu, Y. and Su, R., 2021. Synthesis of Maximally Permissive Covert Attackers Against Unknown Supervisors by Using Observations. arXiv preprint arXiv:2106.12268, Automatica, under review, 2021.
Tai, R., Lin, L., Zhu, Y. and Su, R., 2021. Privacy-Preserving Supervisory Control of Discrete-Event Systems via Co-Synthesis of Edit Function and Supervisor for Opacity Enforcement and Requirement Satisfaction. arXiv preprint arXiv:2104.04299, IEEE Transactions on Automatic Control, under review, 2021.
Tai, R., Lin, L., Zhu, Y. and Su, R., 2021. Synthesis of Covert Sensor Attacks in Networked Discrete-Event Systems with Non-FIFO Channels. arXiv preprint arXiv:2103.07132, IEEE Transactions on Automatic Control, under review, 2021.
Joao Carlos Basilio, Christoforos N. Hadjicostis, Rong Su. Analysis and Control for Resilience of Discrete Event Systems. Foundations and Trends in Systems and Control Series. Now Publishers Inc. 2021.
L. Lin, R. Tai, Y. Zhu, R. Su, Observation-assisted heuristic synthesis of covert attackers against unknown supervisors, Discrete Event Dynamic Systems, under review, 2021.
L. Lin, R. Su (2019). Bounded synthesis of resilient supervisors. IEEE Transactions on Automatic Control, under review, 2020.
L. Lin, R. Su (2020). Synthesis of covert actuator and sensor attackers. Automatica, under review, 2020.
L. Lin, Y. Zhu, R. Su (2020). Synthesis of covert actuator attackers for free. Discrete Event Dynamic Systems, DOI: 10.1007/s10626-020-00312-2. Accepted.
L. Lin, Y. Zhu, R. Su (2019). Towards bounded synthesis of resilient supervisors. Conference on Decision and Control, pp. 7659-7664. Accepted
L. Lin, R. Su (2020). Synthesis of covert actuator and sensor attackers as supervisor synthesis. Workshop on Discrete Event Systems, Accepted
Zhu, Y., Lin, L., & Su, R. (2018). Supervisor Obfuscation Against Actuator Enablement Attack. European Control Conference(2019), Accepted
Aida Rashidinejad, Liyong Lin, Bart Wetzels, Yuting Zhu, Michel Reniers, Rong Su. Supervisory Control of Discrete-Event Systems under Attacks: An Overview and Outlook. European Control Conference(2019), Accepted
Lin, L., Thuijsman, S., Zhu, Y., Ware, S., Su, R., & Reniers, M. (2018), Synthesis of successful actuator attackers on supervisors. American Control Conference (2019), Accepted
Liyong Lin, Rong Su, Bertil Brandin, Simon Ware, Yuting Zhu, Synchronous Composition of Finite Interval Automata. 15th IEEE International Conference on Control and Automation (ICCA, 2019), Accepted
Su, R., (2017). Supervisor synthesis to thwart cyber attack with bounded sensor reading alterations. Automatica, Accepted, April 2017
Projects:
Discrete Event Based Cyber Security Analysis and Attack Resilient Controller Synthesis for Cyber Physical Systems, 2018 - 2021, completed.
Secure and Privacy Preserving Multi-agent Cooperation, 2017 - 2019, completed.